Ethical Hacking - Metasploit
Ethical Hacking - Metasploit Metasploit is one of the most powerful exploit tool…
Ethical Hacking - Enumeration
Ethical Hacking - Enumeration Enumeration belongs to the first phase of Ethical Ha…
Ethical Hacking - Exploitation
Ethical Hacking - Exploitation Exploitation is a piece of programmed software or s…
Defenses against DNS Poisoning | Ethical Hacking - DNS Poisoning
Ethical Hacking - DNS Poisoning DNS Poisoning is a technique that tricks a DNS ser…
 ethical hacking too has a set of distinct phases. It helps hackers to make a structured ethical hacking attack.
ethical hacking too has a set of distinct phases. It helps hackers to make a structured ethical hacking attack.
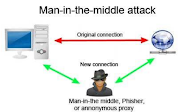
What Is MITM?
What is MITM? The Man-in-the-Middle attack (abbreviated MITM, MitM , MIM, MiM , …
What is ARP Spoofing
What is ARP Spoofing? ARP packets can be forged to send data to the attacker’s mac…
Ethical Hacking - Sniffing Tools | MSN Sniffer |Ethical Hacking - ARP Poisoning
Ethical Hacking - Sniffing Tools There are so many tools available to perform snif…
Lawful Interception
Lawful Interception Lawful Interception (LI) is defined as legally sanctioned acce…
What Is hardware Protocol Analyzers
Hardware Protocol Analyzers Before we go into further details of sniffers, it is …
Types of Sniffing
Types of Sniffing Sniffing can be either Active or Passive in nature. Passive …
 Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools.
Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools.
What can be sniffed? ,Ethical Hacking Sniffing , Ethical Hacking - Sniffing Tools
Ethical Hacking - Sniffing Sniffing is the process of monitoring and capturing all…
Categories
Contact Form
Wikipedia
Tags
- Adware − Adware is software designed to force pre-chosen ads to display on your system 2
- Ethical Hacking - Overview | Certificate Ethical hacking 1
- Hacker Types Hackers can be classified into different categories such as white hat 1
- Learn to C Language 1
- Password 1
- To recover lost information 1
- Types Of Hacking | Network 1
- Website Hacking 1
- Website development 1
- especially in case you lost your password. 1
Popular Posts











